There are three main types of assets that may need to be protected: sensitive data and information, networks, and systems.
Sensitive data and information
Sensitive data and information refers data or information that relates to a local council’s citizens, the organisation itself, or that otherwise concern the secure operation of systems.
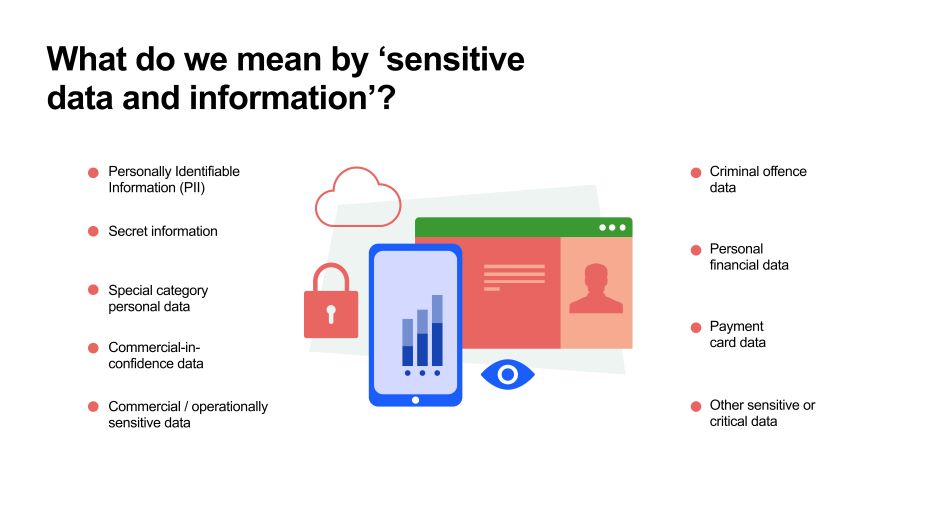
Examples of sensitive data and information
Personally Identifiable Information (PII) - Information that can be used to distinguish or trace an individual’s identity, either alone or when combined with other information that is linked or linkable to a specific individual.
Secret information - Very sensitive information that justifies heightened protective measures to defend against determined and highly capable threat actors. For example, where compromise could seriously damage military capabilities, international relations or the investigation of serious organised crime.
Commercial / operationally sensitive data - information whose loss, misuse, or unauthorised access or modification could adversely affect the commercial or operational security of an organisation
Commercial-in-confidence data - Commercially sensitive information which must be kept confidential between relevant parties for example a supplier’s trade secrets that were shared in confidence with a council
Special category personal data - personal data that needs more protection because it is sensitive according to UK General Data Protection Regulation (GDPR) - this includes racial, religious, biometric and health data
Criminal offence data - personal data relating to criminal convictions and offences or related security measures
Personal financial data - an individual’s personal credit, charge or debit card information; bank account information; band, credit or financial statements; account or PIN numbers and other information relating to an individual’s personal finances.
Payment card data - information used to process credit or debit card transactions
Other sensitive or critical data - any other information whose loss, misuse, or unauthorised access or modification could adversely affect security.
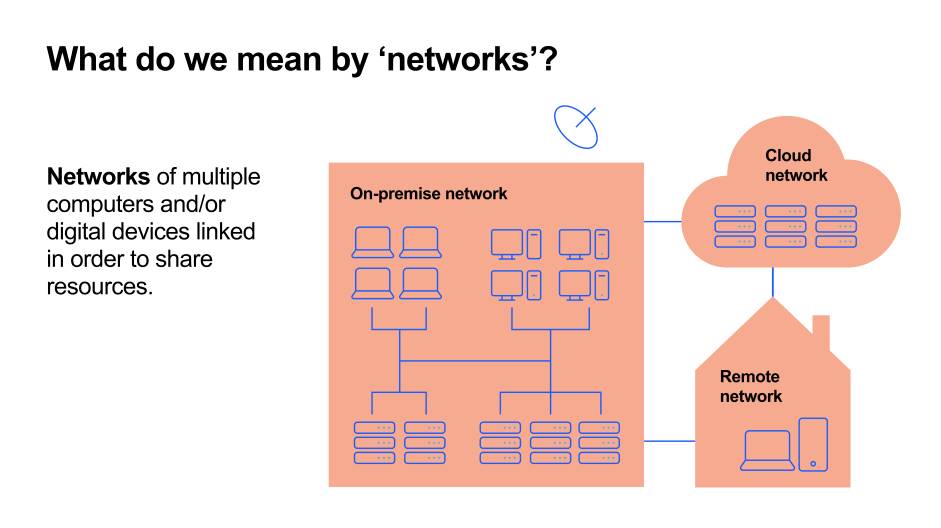
Networks
Networks are two or more computers linked in order to share resources.
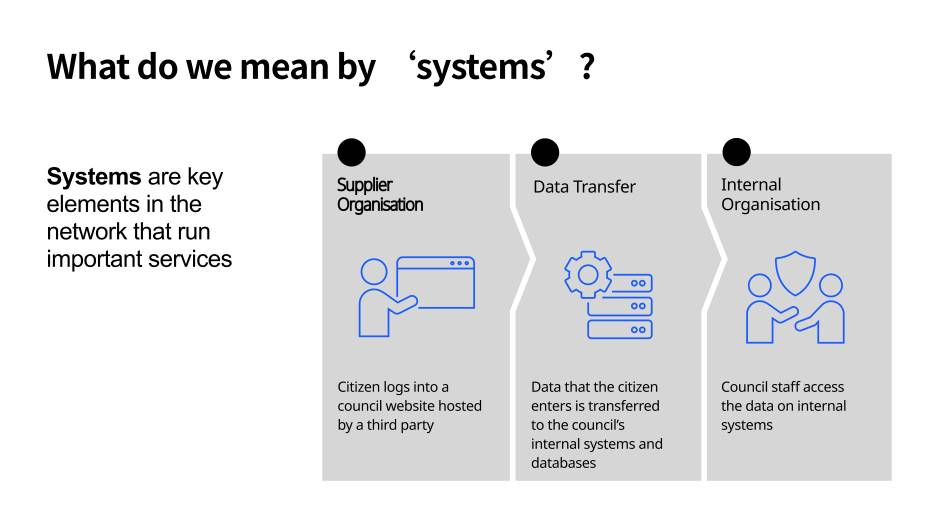
Systems
Systems refer to key elements in the network that run important services, such as housing or contract management systems. Systems can be internal - for example, hosted within a network. And they can also be external - hosted on third party infrastructure.