There are many different ways of monitoring and reporting when it comes to cyber security requirements and controls specific to suppliers and their supply chains.
It is important to remember that subcontractors ought to be considered throughout contract management as well.
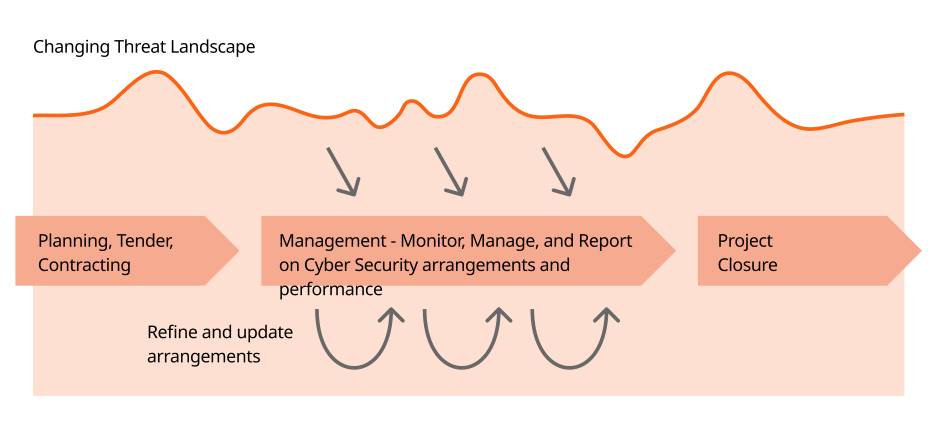
The evolving landscape and life cycle of a contract
The threat landscape is constantly shifting and effective cyber security and resilience requires continuous management and improvement. Risks may change throughout the life cycle of a contract as:
- new vulnerabilities are identified
- new exploits to take advantage of vulnerabilities are developed
- new technologies proliferate.
All of these create new opportunities for threat actors, and make the need for more effective mitigations or controls more urgent.
Over the life cycle of a contract, if you do not have a system to robustly monitor, manage and report on the cyber security arrangements and performance of the supply chain, it might be difficult to embed and maintain resilience.
Work with your suppliers to identify risk and improve cyber security and resilience
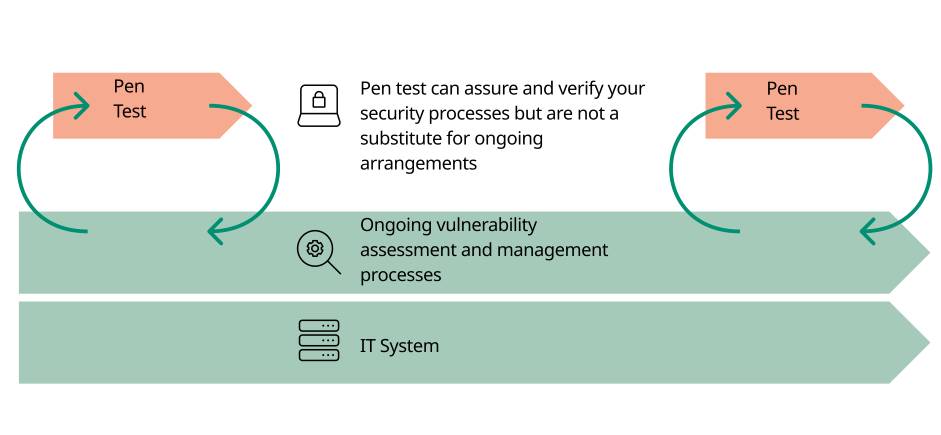
The methods for continual monitoring of a supplier are very similar to or even the same as those used to initially evaluate evidence provided by the supplier.
- Identify where risks are developing or issues exist.
- Take appropriate mitigations to embed cyber resilience.
- Request and evaluate evidence.
- Maintain regular dialogue with suppliers.
- Carry out cyber exercises including simulated attacks and breaches.
- Conduct regular, oftentimes annual, internal reviews.
- Carry out audits including certification reviews, and pen tests.
Penetration test audits
Penetration tests, or ‘pen tests’, as they are sometimes called, are a useful tool for analysing the security of IT systems. However, penetration tests are not a magic bullet for ensuring cyber security and resilience. They can and should be used but simply having a pen test does not make a service or system more secure.
Types of penetration tests
There are numerous types of penetration tests, and this is not a comprehensive list, however the three most important types are outlined below.
- Identification of vulnerabilities in bespoke software including web applications.
- Scenario driven testing aimed at identifying vulnerabilities.
- Scenario driven testing aimed at the detection and response capability.
Speak with your IT team or colleagues to identify whether, for a given contract, penetration testing is appropriate, and if so, what types of penetration testing might be most appropriate.
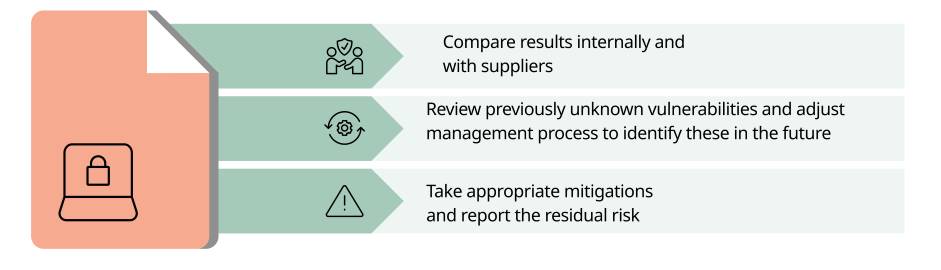
Evaluating penetration test results
The output of a penetration test can be confusing, but you should openly discuss any results with your internal IT teams, vulnerability arrangement group and suppliers.
Compare the results with your and your suppliers internal tests. The pen test provider may not have had access to all information and you need to verify the results and the associated impact.
- Any previously unknown vulnerabilities need to be assessed and the process for ongoing management needs reviewing to understand why these vulnerabilities were missed by the ongoing management process.
- Suitable mitigation needs to be taken for vulnerabilities. Patches ought to be performed where available and able. These may not always be the actions recommended by the pen test report.
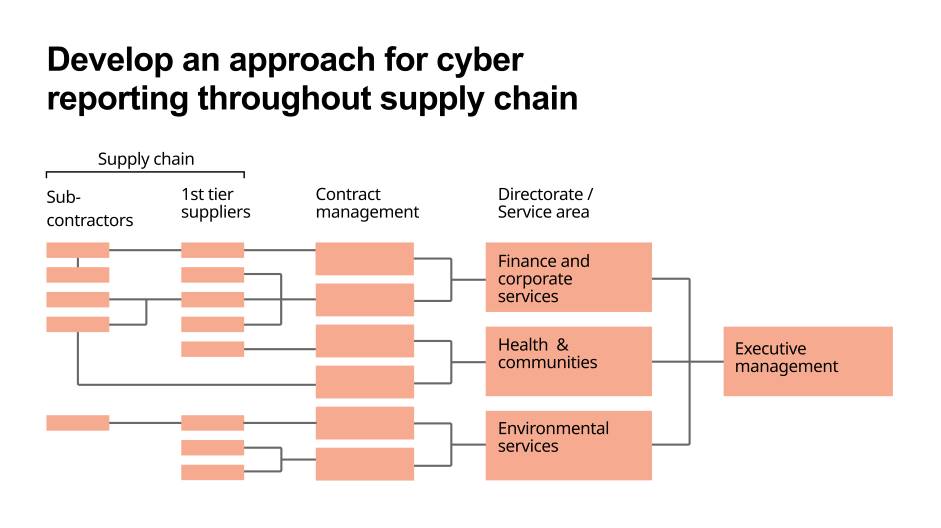
Develop an approach for cyber security reporting throughout the supply chain
Cyber reporting across the supply chain is a key enabler to embedding cyber resilience and security. Reporting can only be effective if there is a clear governance structure with defined roles and responsibilities - from subcontractors and suppliers, to direct suppliers, all the way up to local council senior executive level. Any reporting method should be consistently applied throughout the organisation and supply chain. Reporting only on a subsection of the supply chain may direct resources away from more critical or riskier parts of the supply chain that are invisible to the reporting structure.
Steps for reporting on cyber across the supply chain
- Define success criteria and metrics for cyber reporting and get agreement on these with both the senior management teams and suppliers.
- Define simple templates that can be used by your suppliers to report to you and subsequently you can use to aggregate that data and report to senior management. Templates need to be simple and achievable, and applied consistently at an appropriate cadence.
- Align reporting to your governance arrangement so that information is timely and relevant when reported up to senior management.
- Define a governance and escalation route. Reporting should be used to draw attention to the greatest risks but also communicate the challenges you and your supply chain face in addressing these risks.